News Release Archives
Note that the releases are accurate at the time of publication but may be subject to change without notice.
FOR IMMEDIATE RELEASE No. 3002
Mitsubishi Electric Develops Cyber Attack Detection Technology
Preventing information leakage by monitoring behavior patterns typical of viruses
TOKYO, February 17, 2016 - Mitsubishi Electric Corporation (TOKYO: 6503) announced today it has developed a cyber-attack detection technology that can classify computer virus behavior into about 50 different patterns. Symantec's latest report on Internet security suggests a million new viruses are spawned every day, but Mitsubishi Electric's new technology offers the capability of detecting even previously unknown viruses through their behavior, preventing information leakage and its associated damages.

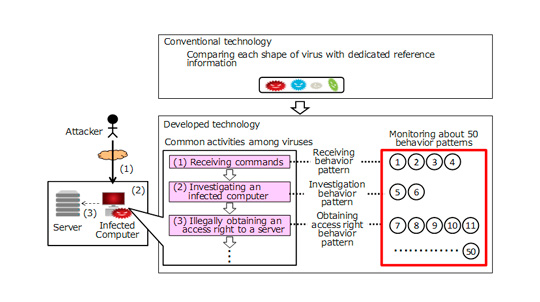

During a cyber attack, the virus has to take several steps, such as infecting a targeted computer, receiving commands from the attacker, investigating the infected computer, and then illegally obtaining access rights to further expand its activities. Each of those steps also has a set of associated behavior patterns. For example, when investigating an infected computer, the attacker determines which information should be obtained and how by searching documents, finding communication routes, and checking the configuration of security measures. Mitsubishi Electric has identified about 50 behavior patterns, and has defined dedicated log analysis rules for each that allow the system to monitor suspicious activity and accurately detect a virus for preventing information leakage. While the number of new viruses each year grows astronomical, a dozen common behavior patterns are expected to evolve each year. These patterns can quickly be added to the detection system, stopping all new viruses that might seek to exploit the pattern.

Previously, it was hard to distinguish legitimate activities from a malicious cyber attack. Mitsubishi Electric's new technology defines a sequence of behaviors as a cyber-attack scenario. By using correlation analysis to determine whether a particular sequence of activities follows the scenario or not, the technology is able to distinguish between legitimate activities that follow similar patterns and actual cyber attacks.

Previously, it was hard to distinguish legitimate activities from a malicious cyber attack. Mitsubishi Electric's new technology defines a sequence of behaviors as a cyber-attack scenario. By using correlation analysis to determine whether a particular sequence of activities follows the scenario or not, the technology is able to distinguish between legitimate activities that follow similar patterns and actual cyber attacks.
Inquiry
Customer Inquiries
Mitsubishi Electric Corporation