Information Security
Basic Policy
In order to respond to the threat of cyberattacks, which are rapidly becoming more sophisticated and diverse, the Mitsubishi Electric Group is continually working to strengthen its cybersecurity and governance of information management and operations.
We manage the information entrusted to us by customers and stakeholders of Mitsubishi Electric as well as confidential corporate information, including sales, engineering, and intellectual property information, based on the Declaration of Confidential Corporate Information Security Management.
Information Security Organization Structure
The Mitsubishi Electric Group’s information security framework designates the President & CEO as the Chief Officer responsible for information security management. It consists of a corporate division that manages information security across the organization and business divisions that bear responsibility for information security risks within their business activities. Within the corporate division, an Executive Officer in charge of Information Security appointed as the Officer, Information Security of MELCO*1 Group oversees all aspects of information security management. Under the direction, the Chief Information Security Manager ensures compliance with customer supply chain requirements, international standards, and industry best practices, while regularly reporting on the division’s activities. In each business division, General Managers, Information Security operate under the supervision of their respective Officer, Information Security to manage information security of their own divisions, including oversight of associated companies.
The Officer, Information Security of MELCO Group convenes regular Information Security Management Meetings with General Managers, Information Security to communicate and coordinate the formulation of group-wide information security policies and the planning of related initiatives.
Each division is equipped with functions for information management: CSIRT,*2 PSIRT,*3 and FSIRT.*4 The Corporate Information Security Division is responsible for planning and promoting the Group’s information security mechanisms, rules, IT system security, and compliance with personal data protection laws and regulations. In the event of a security incident, this division collaborates with the relevant business divisions to make prompt and informed decisions based on operational circumstances, ensuring swift incident response.
As for cybersecurity issues at overseas associated companies, the Corporate Information Security Division cooperates closely with overseas regional representative managers in the Americas, Europe, and Asian countries, while considering each region’s unique circumstances.
- 1 Mitsubishi Electric Corporation
- 2 Computer Security Incident Response Team
- 3 Product Security Incident Response Team
- 4 Factory Security Incident Response Team
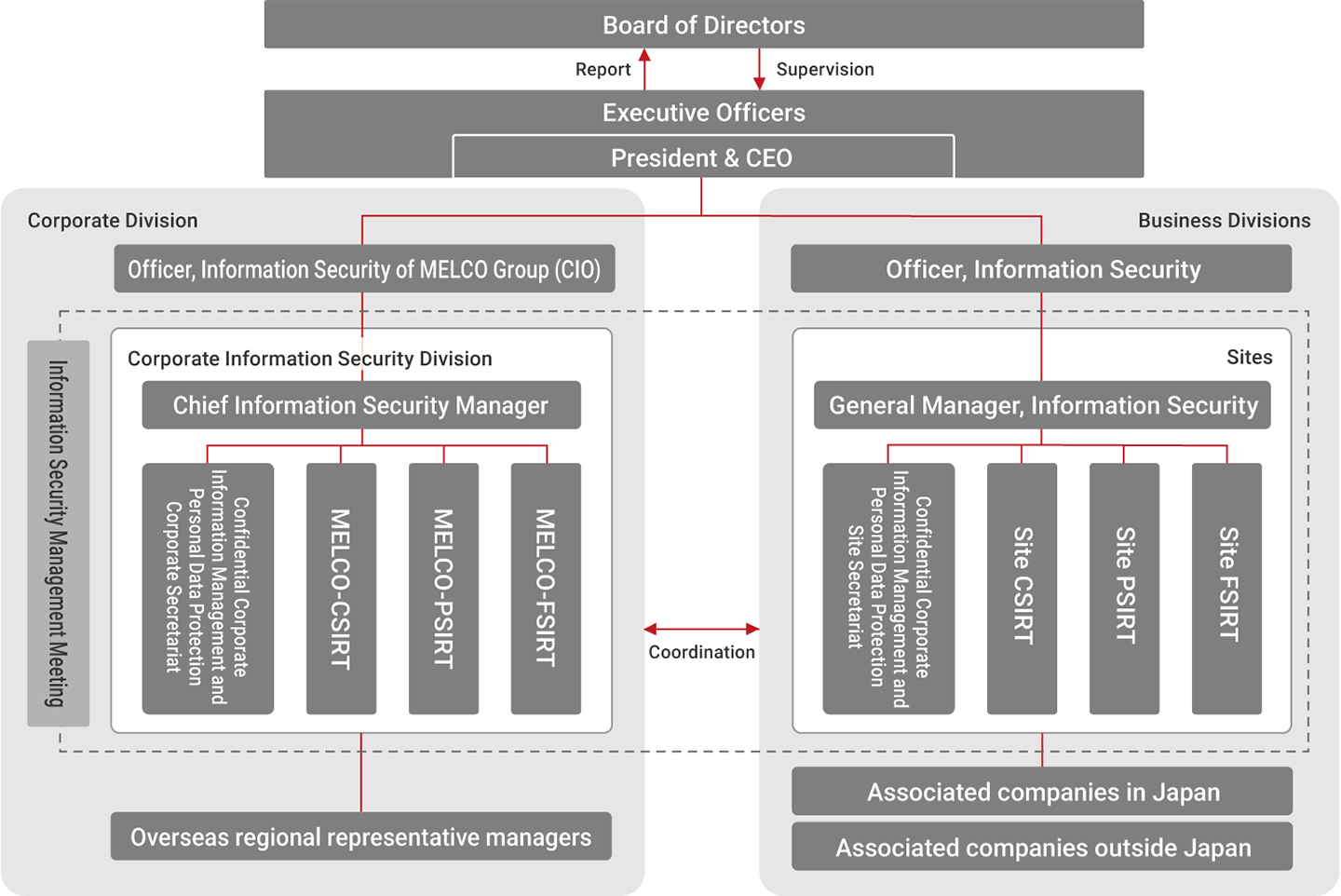 Information Security Organization Structure (Mitsubishi Electric Group)
Information Security Organization Structure (Mitsubishi Electric Group)
Personal Information Protection
Mitsubishi Electric has established a Personal Information Protection Policy and Company Rules on Personal Information Protection, developing a framework in accordance with the Japanese Industrial Standards JIS Q 15001: Personal Information Protection Management System – Requirements. Through this framework, the Company ensures thorough awareness of personal information protection among its employees and actively promotes initiatives to safeguard personal information.
In January 2008, we were granted the right to use the PrivacyMark, which certifies the establishment of management systems that ensure proper measures for personal information protection. We have been renewing the PrivacyMark certification since then. In January 2024, we completed the eighth PrivacyMark renewal process.
Cyberattack Countermeasures
To counter cyberattacks against companies, the Mitsubishi Electric Group is implementing centralized management of networks, computer terminals, and servers (cloud) and adopting defense-in-depth. Defense-in-depth provides protection against cyberattacks and enables the detection of suspicious activities and intrusions. The immediate response system we have established also helps to prevent and minimize damage.
In order to support work at the office as well as work requiring access from home or on a business trip, strong multifactor authentication has been introduced and authentications are centrally managed. Internet websites are constantly exposed to many external threats, and so we only launch websites that are approved in order to maintain a high security level.
