- Research & Development
FOR IMMEDIATE RELEASE No. 3649
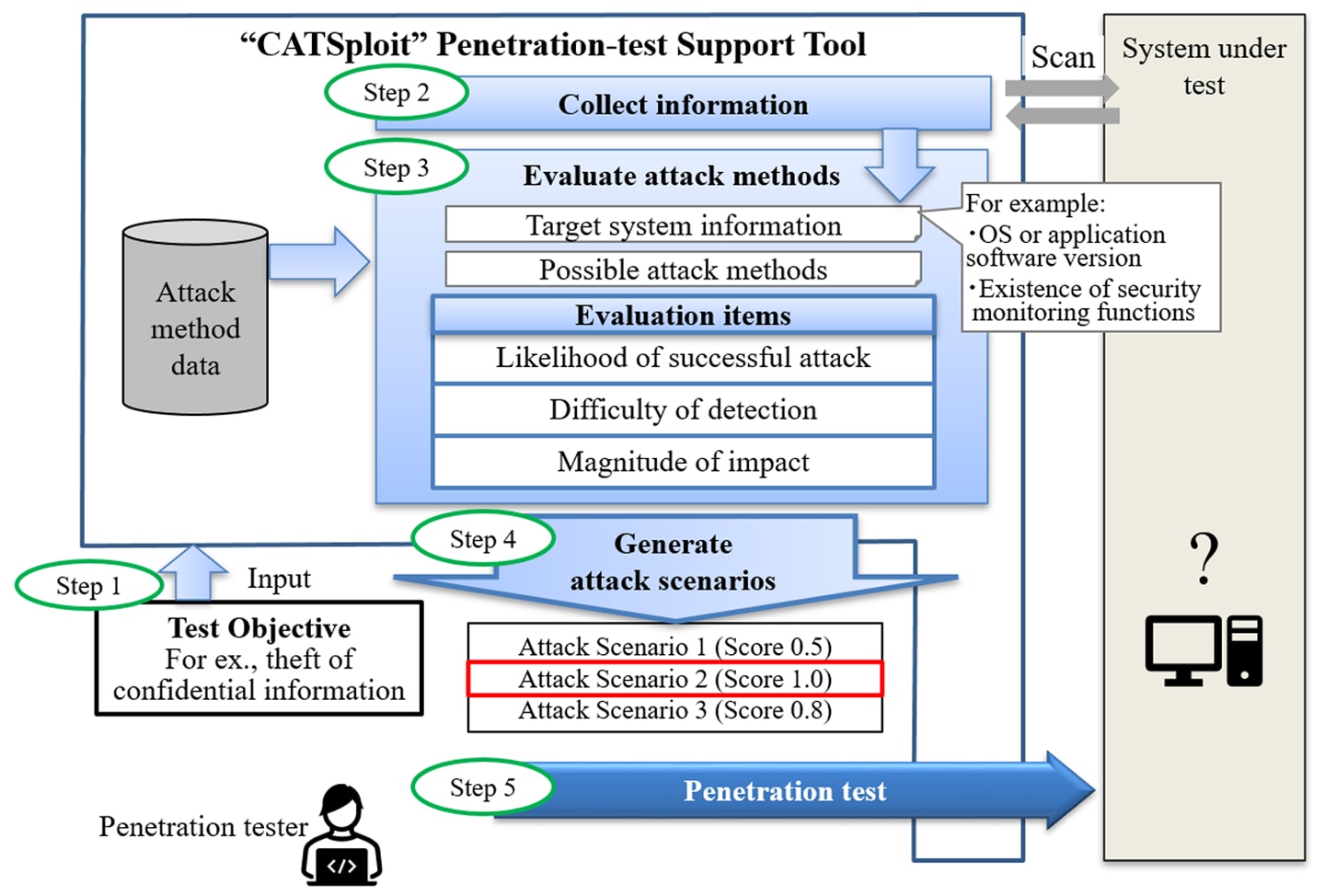
Usage example of the support tool during penetration testing
TOKYO, December 5, 2023 - Mitsubishi Electric Corporation (TOKYO: 6503) announced today that it has developed the world's first1 penetration-test2 support tool, CATSploit, which automatically generates attack scenarios based on the test objectives of a penetration tester, such as the theft of confidential information, to evaluate the effectiveness of test attacks. Using the attack scenarios and resulting test results (scores), even inexperienced security engineers can easily perform penetration tests.
In recent years, control systems including infrastructure, factory equipment, etc., have become increasingly connected to networks, raising the risk of disruptions, such as power outages or public transportation shutdowns, due to cyberattacks. The need to implement security measures in such systems has become urgent. In addition, ISA/IEC 624433 standards require that fuzzing4 and penetration security tests be performed on systems and equipment to evaluate their resistance to cyberattacks, including vulnerabilities due to implementation or configuration errors. Penetration testing is highly sophisticated and requires the involvement of white-hat hackers5 to actually attack the system or product being tested, but such individuals, who must possess very high levels of expertise, are scarce and difficult to find.
Mitsubishi Electric, by focusing on the factors that white-hat hackers consider when selecting their attack vectors, has now developed a penetration-test support tool that generates lists of possible attack scenarios and their effectiveness (expressed as numerical scores).
Details of the tool will be presented on December 6 (11 am local time) during the Black Hat Europe 2023 Arsenal in London, which will take place on December 6 and 7.
- 1According to Mitsubishi Electric's research as of December 5, 2023
- 2Test to confirm that if a system or equipment can be compromised by an actual attack
- 3Security Standards for Industrial Control Systems
- 4A test method for detecting software defects or vulnerabilities by entering invalid or incorrect data
- 5Ethical hackers who use advanced knowledge and computer technology to identify security issues, etc.
Inquiry
Media contact
Customer Inquiries
Related articles
- Research & Development
-
Apr 24, 2025
-
Mar 27, 2025
-
Mar 13, 2025
